by Krieger | Jan 27, 2020 | HT BLOG
If you’ve ever wanted to conceal your identity or protect your personally identifying information from prying eyes, then this series is made specifically for you. Installment 1: CONCEALING YOUR TRUE PHONE NUMBER Have you ever shared your phone number with someone and...

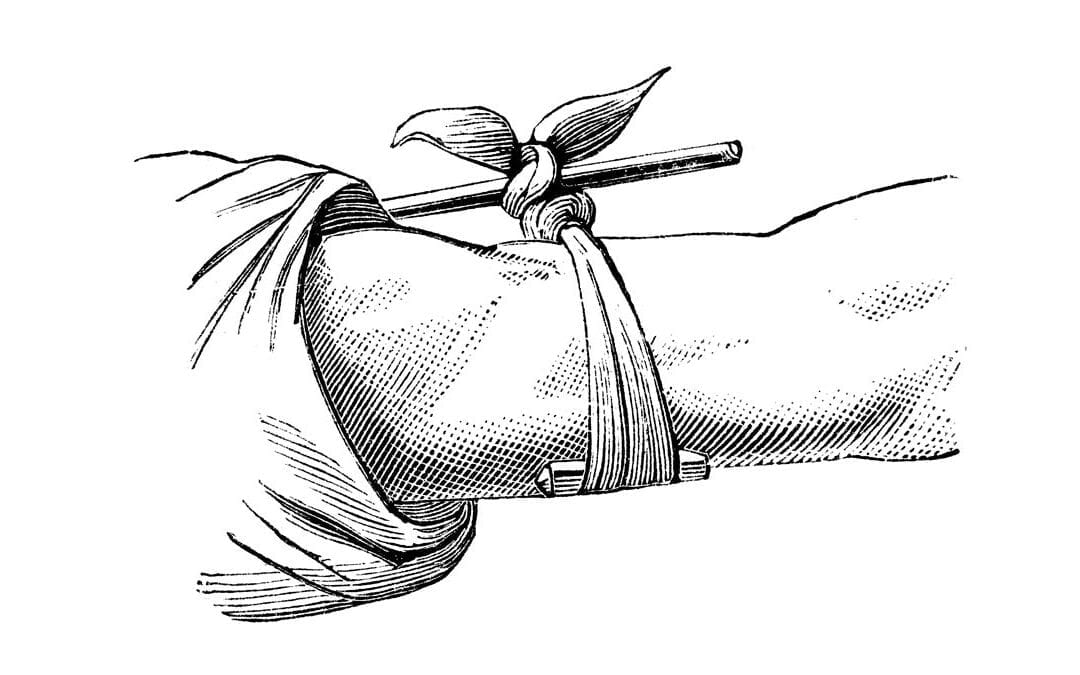
by Krieger | Jun 17, 2019 | HT BLOG, MEDICAL
HISTORY In 2018 my two step-sons (we’ll call them Adam and John) took a cross-country trip to visit me in Florida. While in Florida, we took the opportunity to enjoy the great outdoors of the sunshine state by doing some wave running, eating seafood, throwing axes,...

by Krieger | Apr 17, 2019 | CYBER SECURITY, HT BLOG
HYBRID TACTICS ASYMMETRIC CYBER SECURITY COURSE Email: [email protected] 254.522.9062 Prevent unauthorized persons from accessing, or forcing you to reveal your private messages, shared communication, or stored information. Have the confidence in knowing that the...

by Krieger | Apr 16, 2019 | CYBER SECURITY, HT BLOG
HYBRID TACTICS ASYMMETRIC CYBER SECURITY COURSE Email: [email protected] 254.522.9062 The cyber world is the new hacker’s big game target for those who seek to access the ultimate online prize: Your Personally Identifying Information, photographs, and shared...

by Krieger | Apr 13, 2019 | CYBER SECURITY, HT BLOG
HYBRID TACTICS ASYMMETRIC CYBER SECURITY COURSE Email: [email protected] 254.522.9062 Your cellular phone and personal computer are two of the key targets selected by hackers in order to attain your personally identifying information, leading to compromise of...

by Krieger | Feb 13, 2019 | CYBER SECURITY, HT BLOG
HYBRID TACTICS ASYMMETRIC CYBER SECURITY COURSE Email: [email protected] 254.522.9062 Your cellular phone and personal computer are two of the key targets selected by hackers in order to attain your personally identifying information, leading to compromise of...